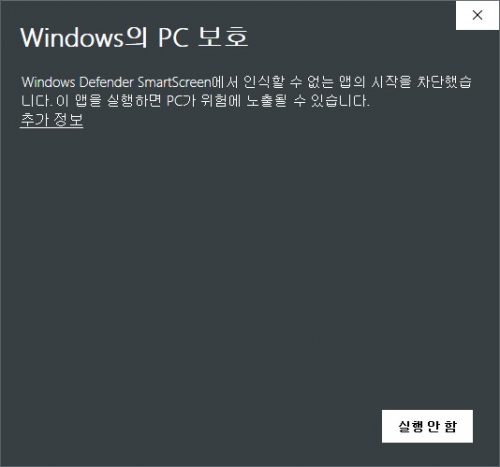
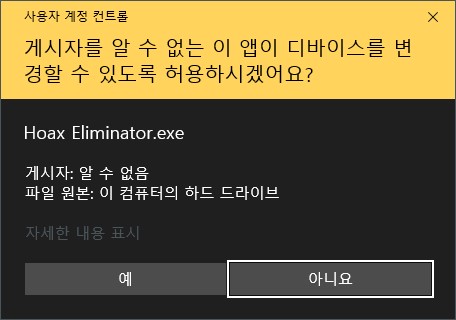
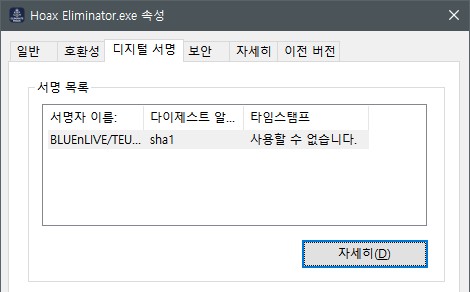
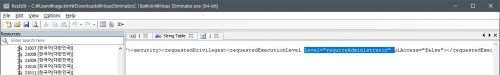
You might be seen UAC controlled or WIndows defender protection dialog for some application for Windows as like this:
– or –
It meant your application requires administrator privilege but doesn’t contained secured certification information in manifest block of EXE inside resource.
Here’s an application to testing a simple cmd or batch file script of Windows for automatically accepts administrator privilege invoking.
Hoax Eliminator is an application for clean up defected Windows system by all fault(or fake) security web based NAPI plug-in garbages in South Korea. All internet financial web services requires useless fault security garbages installation for every Windows and Mac OSX (or even some Linux) to avoids sandbox security of modern web browsers, and we are named fault or fake security plug-ins as “Hoax”, and “Hoax Eliminator” helps uninstall all these fakes in a click.
But “Hoax Elminiator” not using common certification authority, it may just self-signed tool that belong to cert-tool or Signtool in Visual Studio.
So user need to see UAC warning dialog in everytime to running this application, but here’s a simple tip to avoids checking UAC dialog asking with this:
cmd /min /C "set __COMPAT_LAYER=RUNASINVOKER && start "" %1"
Write above scripts into a file that named as you want but extension must be one of these “.bat” or “.cmd”. and save it then, drag “Hoax Eliminator.exe” to your script file ( eg. “run_as_invoker.cmd” ) in explorer. You may not see a dialog asking about UAC.
“Hoax Eliminator” included manifest information with “requireAdministrator” in requested execution level section as below:
And my simple script may covers running without UAC dialog specially not contains common certifications. But don’t make it used be abused for skipping UAC dialog. It may not works for all time – specially in boot sequence.